How To Use SSH IoT From Anywhere: Login To Mac Without Hassle
So, you're here because you want to know how to use SSH IoT from anywhere and log in to your Mac without any hassle. Let me tell you, this is one of those game-changing skills that every tech-savvy person should have in their arsenal. Imagine being able to access your Mac from anywhere in the world, whether you're chilling on a beach in Bali or stuck in a meeting room in Berlin. Sounds pretty cool, right? Well, buckle up, because we're about to dive deep into the world of SSH and IoT.
Before we get into the nitty-gritty, let's break it down for those who might be scratching their heads. SSH, or Secure Shell, is like a super-secret tunnel that lets you remotely access and control your computer from anywhere. Combine that with IoT (Internet of Things), and you've got yourself a powerful combo that can make your life so much easier. And guess what? You don't need a degree in computer science to do it. Stick around, and I'll show you how it's done.
Now, I know what you're thinking. "Is this really safe? Can I trust SSH?" The short answer is yes, absolutely. When used correctly, SSH is one of the most secure ways to access your devices remotely. But of course, there are a few things you need to keep in mind to make sure your data stays safe. We'll cover all that and more as we go along. So, are you ready to level up your tech game? Let's get started!
Why SSH IoT Matters in Today's World
In today's fast-paced world, being able to access your devices remotely is more important than ever. Whether you're a freelancer working from home, a business owner managing servers, or just someone who likes to tinker with gadgets, SSH IoT can make your life so much easier. Imagine being able to troubleshoot your home network from across the globe or access important files on your Mac without having to physically be there. Sounds pretty convenient, doesn't it?
But it's not just about convenience. Security is a huge concern in the digital age, and SSH provides a secure way to access your devices without exposing them to potential threats. By using SSH, you can ensure that your data remains safe and secure, even when you're accessing it from public Wi-Fi or other potentially unsafe networks. And with the rise of IoT devices, being able to manage them remotely is becoming increasingly important.
Understanding SSH: The Basics
So, what exactly is SSH? At its core, SSH is a protocol that allows you to securely access and control remote devices over a network. Think of it like a secret handshake that only your computer and the device you're trying to access can understand. This handshake ensures that your data remains encrypted and secure, even when it's traveling across the internet.
One of the coolest things about SSH is that it works on virtually any device that supports it. Whether you're using a Mac, PC, or even a Raspberry Pi, SSH can help you connect to your devices from anywhere in the world. And the best part? It's free! There are no expensive licenses or subscriptions to worry about. All you need is a little bit of know-how, and you're good to go.
Key Features of SSH
- Secure data transfer using encryption
- Remote access to devices over the internet
- Support for multiple authentication methods
- Compatibility with a wide range of devices
What Is IoT and How Does It Relate to SSH?
Now, let's talk about IoT. IoT stands for Internet of Things, and it refers to the growing network of interconnected devices that can communicate with each other over the internet. From smart thermostats to security cameras, IoT devices are becoming increasingly common in our daily lives. And while they offer a ton of convenience, managing them can sometimes be a challenge.
This is where SSH comes in. By using SSH, you can remotely access and manage your IoT devices from anywhere in the world. Whether you need to update firmware, troubleshoot issues, or just check on the status of your devices, SSH makes it easy to do so without having to physically be there. And because SSH is secure, you can rest assured that your devices and data are protected from prying eyes.
Benefits of Combining SSH and IoT
- Remote management of IoT devices
- Improved security for connected devices
- Increased flexibility and convenience
- Cost-effective solution for device management
How to Set Up SSH on Your Mac
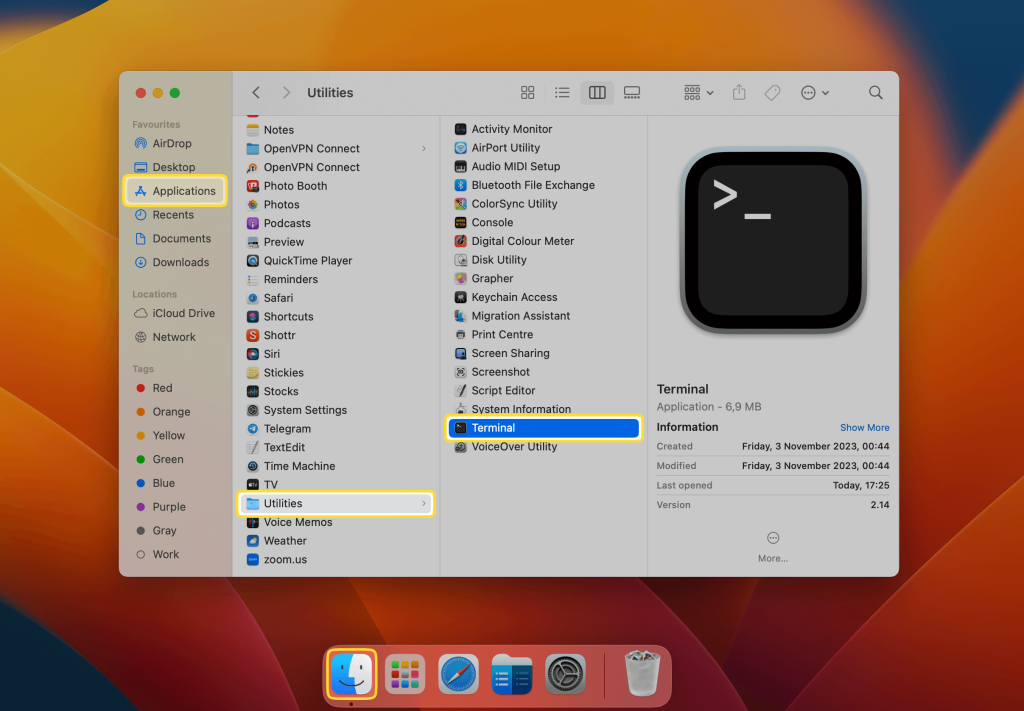
Alright, let's get down to business. The first step in using SSH IoT from anywhere is setting up SSH on your Mac. Don't worry, it's not as complicated as it sounds. In fact, most Macs come with SSH pre-installed, so all you need to do is enable it. Here's how:
- Open System Preferences on your Mac
- Click on "Sharing" and then select "Remote Login"
- Make sure the checkbox next to "Allow remote login" is ticked
- That's it! Your Mac is now ready to accept SSH connections
Of course, there are a few extra steps you can take to make sure your setup is as secure as possible. For example, you can configure SSH to use public key authentication instead of passwords, which adds an extra layer of security. We'll cover that in more detail later on.
Tips for Securing Your SSH Connection
- Use strong passwords or public key authentication
- Limit access to specific IP addresses if possible
- Disable password authentication for added security
- Keep your SSH software up to date
Connecting to Your Mac from Anywhere
Now that you've got SSH set up on your Mac, it's time to connect to it from anywhere in the world. There are a few different ways to do this, but the most common method is to use an SSH client. If you're using a Mac or Linux machine, you can use the built-in Terminal app to connect. For Windows users, there are several great SSH clients available, such as PuTTY or MobaXterm.
Here's how to connect using the Terminal app:
- Open Terminal on your Mac
- Type "ssh username@your-mac-ip-address" and press Enter
- Enter your password when prompted
- You're now connected to your Mac!
Of course, if you want to connect from outside your local network, you'll need to set up port forwarding on your router. This allows you to access your Mac using its public IP address, rather than just its local IP address. We'll cover how to do that in the next section.
Setting Up Port Forwarding
Port forwarding can be a bit tricky, but it's not impossible. Here's a quick guide to help you set it up:
- Log in to your router's admin interface
- Find the port forwarding settings and create a new rule
- Set the external port to 22 (the default SSH port)
- Set the internal IP address to your Mac's local IP address
- Save the rule and test your connection
Best Practices for Using SSH IoT
Now that you know how to set up and use SSH IoT, let's talk about some best practices to keep in mind. First and foremost, always prioritize security. This means using strong passwords, enabling two-factor authentication whenever possible, and keeping your SSH software up to date. You should also regularly monitor your connections to ensure that no unauthorized access is taking place.
Another important tip is to document your setup. Write down your IP addresses, port numbers, and any other relevant information so that you don't have to remember it all in your head. This will save you a lot of time and frustration in the long run. And finally, don't be afraid to experiment and learn new things. The more you use SSH IoT, the more comfortable you'll become with it.
Common Mistakes to Avoid
- Using weak passwords or no authentication
- Forgetting to update your SSH software
- Not securing your router properly
- Ignoring potential security threats
Advanced SSH Techniques
Once you've got the basics down, you might want to explore some of the more advanced features of SSH. For example, you can use SSH tunnels to securely access other services, such as databases or web servers. You can also set up SSH keys for passwordless authentication, which makes connecting to your devices even easier. And if you're feeling really adventurous, you can even automate your SSH connections using scripts.
Of course, these advanced techniques require a bit more knowledge and experience, so don't be discouraged if you don't get it right the first time. The key is to keep learning and experimenting until you find what works best for you.
SSH Tunneling Explained
SSH tunneling is like creating a secure tunnel between two devices, allowing you to access services that would otherwise be inaccessible. For example, you could use an SSH tunnel to securely access a database running on your Mac from another device. Here's how to set it up:
- Open Terminal on your Mac
- Type "ssh -L local_port:destination_host:destination_port username@your-mac-ip-address" and press Enter
- Enter your password when prompted
- You're now connected via an SSH tunnel!
Conclusion: Take Your Tech Skills to the Next Level
And there you have it, folks! You now know how to use SSH IoT from anywhere and log in to your Mac without any hassle. Whether you're a tech enthusiast, a business owner, or just someone who likes to stay connected, SSH IoT is a powerful tool that can make your life so much easier. Just remember to prioritize security, document your setup, and keep learning new things.
So, what are you waiting for? Go ahead and give it a try! And if you found this article helpful, don't forget to share it with your friends and followers. Who knows? You might just inspire someone else to level up their tech skills too. Happy SSH-ing, and see you on the internet!
Table of Contents
- How to Use SSH IoT from Anywhere: Login to Mac Without Hassle
- Why SSH IoT Matters in Today's World
- Understanding SSH: The Basics
- What Is IoT and How Does It Relate to SSH?
- How to Set Up SSH on Your Mac
- Connecting to Your Mac from Anywhere
- Best Practices for Using SSH IoT
- Advanced SSH Techniques
- Conclusion: Take Your Tech Skills to the Next Level